The systematic management of software updates is a critical function of cybersecurity and operational stability within any modern enterprise. This musing puts forth a structured methodology for the deployment of Windows operating system patches, addressing the architectural choices for update distribution, the temporal cadence of deployment, the empirical validation of updates through phased rollouts, and the management of endpoint reboots to ensure patch finalization. The objective is to provide a defensible and repeatable framework that minimizes the attack surface introduced by software vulnerabilities while mitigating the operational risks inherent in system modification.
A Temporal Strategy for Deployment Cadence
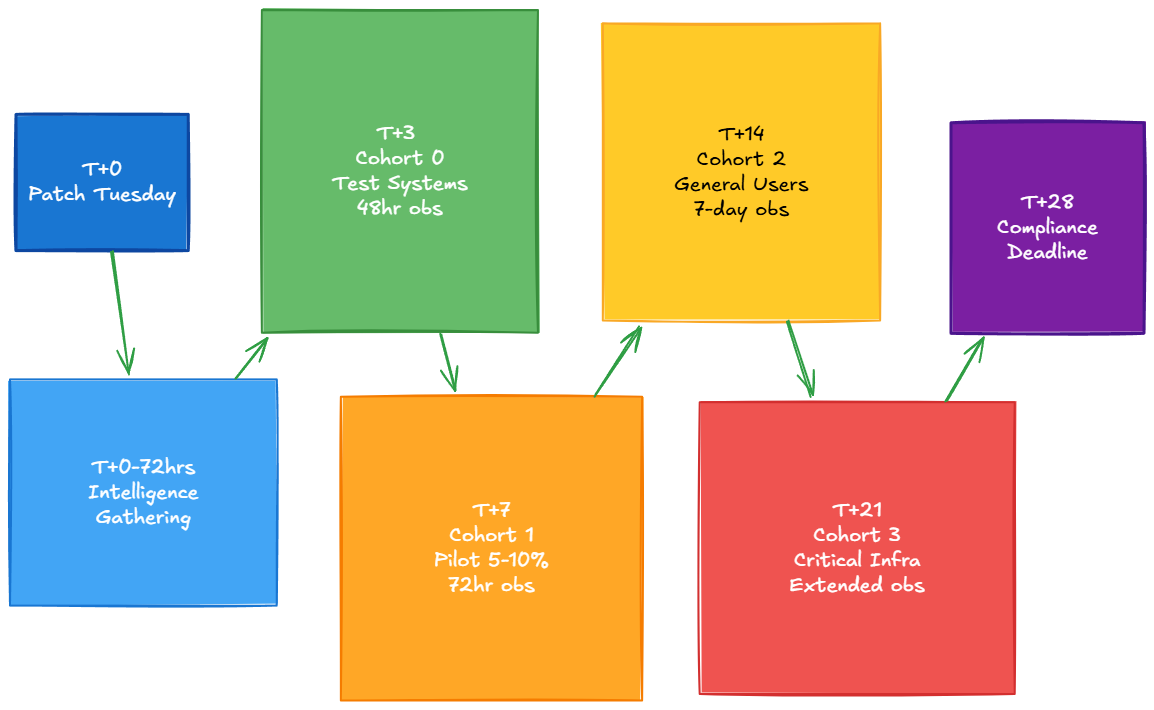
An effective patching strategy is not merely reactive; it is a premeditated rhythm of activity synchronized with Microsoft's monthly update release cycle, colloquially known as "Patch Tuesday" (Tuesday of each month).
Phase I: Intelligence Gathering (T+0 to T+72 hours): Upon release, a moratorium on deployment is observed. This period is dedicated to monitoring industry intelligence sources for reports of adverse impacts or faulty patches. It allows the global IT community to function as an initial, large-scale testbed, mitigating the risk of deploying a problematic update prematurely.Phase II: Structured Deployment (T+72 hours to T+28 days): Following the observation period, the structured deployment process begins, guided by the phased validation model described in Section 3.0.Phase III: Compliance Deadline (T+28 days): The operational goal is to achieve near-100% compliance for all approved patches across the managed fleet before the commencement of the subsequent month's release cycle.
Empirical Validation Through Phased Deployment Cohorts
To mitigate the risk of business disruption from a faulty patch, updates must be validated against production systems in a controlled, progressive manner. This is achieved by segmenting the entire endpoint fleet into distinct deployment cohorts (or "rings"), with progression to the next cohort contingent upon a successful observation period in the current one.
Cohort 0 (Initial Validation): Comprises non-production assets, including dedicated test virtual machines and the systems of IT personnel. This cohort serves to identify catastrophic failures, such as boot issues or major application incompatibility.
Deployment Target: T+3 days. Observation Period: 48-72 hours
Cohort 1 (Pilot Group): A statistically significant and representative sample of users from various business units (e.g., 5-10% of the user base). This cohort is designed to uncover workflow-specific or line-of-business application conflicts that would not be apparent in an IT-only test.
Deployment Target: T+7 days. Observation Period: 5-7 days
Cohort 2 (Broad Deployment): The general population of endpoints. Deployment to this cohort proceeds only after the updates have been validated in Cohorts 0 and 1 with no significant issues reported.
Deployment Target: T+14 days
Cohort 3 (Critical Infrastructure): Includes high-value assets such as domain controllers, database servers, and core application servers. Due to their low tolerance for unplanned downtime, these systems are patched last, after an update has been thoroughly vetted across the entire organization.
Deployment Target: T+21 days or during a pre-scheduled maintenance window
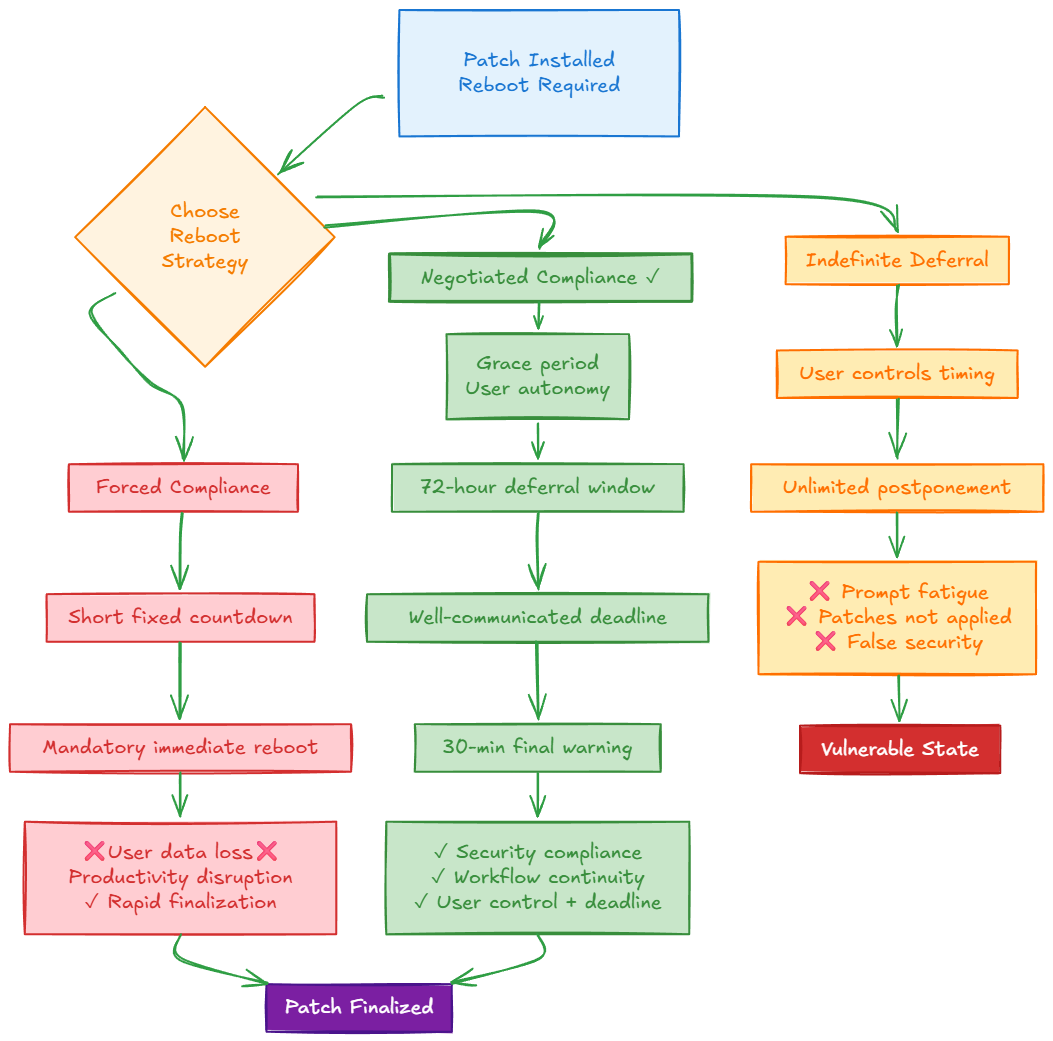
Endpoint State Management: Reboot Methodologies
Many critical patches modify kernel-level components and do not take full effect until the operating system is restarted. Therefore, managing the reboot process is not an administrative triviality but a critical component of patch finalization.
Forced Compliance Model: This strategy enforces a mandatory reboot after a short, fixed countdown. While it ensures rapid patch finalization, it often results in user data loss and productivity disruption, making it an unsuitable primary strategy for user workstations.Indefinite Deferral Model: This strategy allows users to postpone reboots without limit. It leads to "prompt fatigue," where notifications are ignored, and results in a fleet of machines where patches are installed but not fully applied, creating a false sense of security and a persistent state of vulnerability.Negotiated Compliance Model: This is the optimal strategy. It provides the user with a window of autonomy during which they can initiate the reboot at their convenience. This window is followed by a non-negotiable, well-communicated deadline, at which point a forced reboot is initiated. This model balances operational requirements for security with the user's need for workflow continuity. For example, allowing a user to defer for up to 72 hours, after which a mandatory reboot is scheduled with a final 30-minute warning.