There’s a raw, almost brutalist elegance to the BitTorrent protocol. In a world of carefully managed client-server interactions, it stands out as a testament to pure, decentralized engineering. It solves the problem of large-scale file distribution by turning every consumer into a distributor. It works, and it works beautifully. But its design philosophy prioritizes efficiency over all else, leading to inherent architectural trade-offs in privacy and consistency.
For years, the solution was to layer other tools on top—VPNs for privacy, seedboxes for performance. These are functional patches. But a far more elegant solution has emerged in the form of debrid services. On the surface, they look like simple download helpers. But if you look deeper, you'll find a fascinating architectural pattern: a clever abstraction layer that refactors the entire P2P relationship.
Deconstructing the Baseline: The Purity of the Swarm
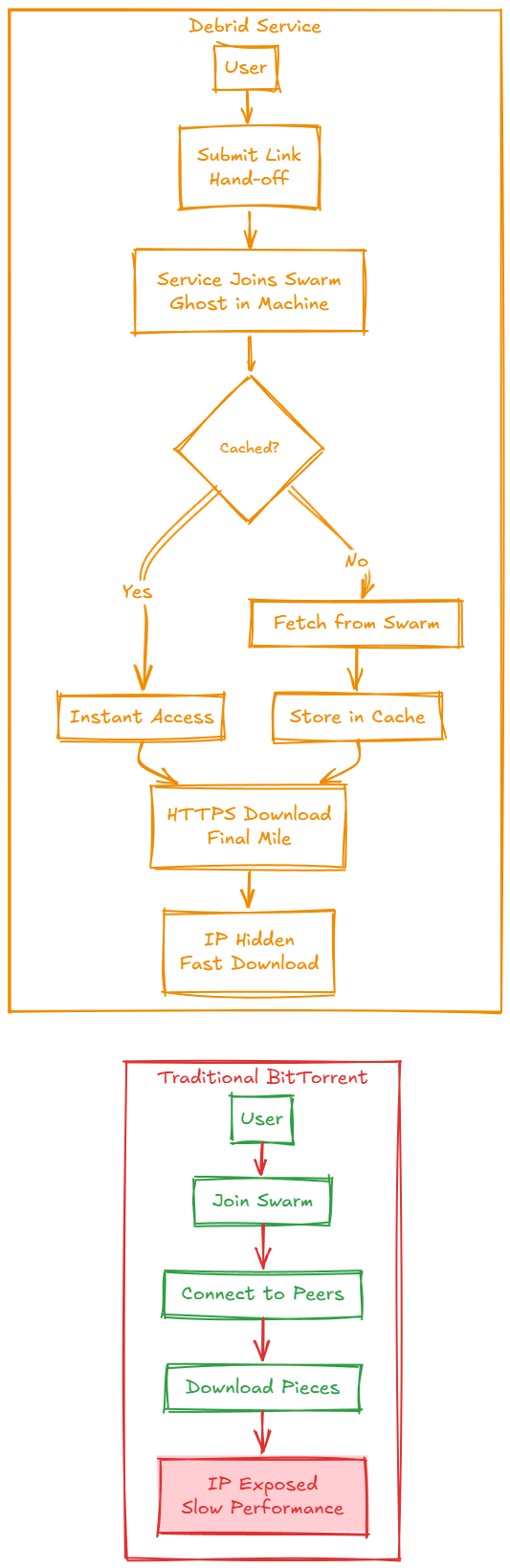
Before we can appreciate the abstraction, we have to respect the foundation. BitTorrent is pure peer-to-peer. When you join a swarm, your client talks to a tracker to find other peers, and then you connect directly to them. You trade file pieces until you have the whole.
The critical design points are:
Performance is communal: Your speed is a function of the swarm's collective upload capacity. You are entirely at the mercy of the swarm's health.
Identity is public: To trade pieces, everyone needs to know everyone else's address. Your IP address is your identity in the swarm, visible to all.
There is no intermediary. It’s a raw, direct, and highly efficient system, but one that leaves the user’s identity exposed and their performance subject to the whims of the crowd.
Enter the Intermediary: The Debrid Architectural Pattern
A debrid service like Real-Debrid introduces a powerful intermediary. It doesn't change the BitTorrent protocol itself; it just changes who participates in it. The core principle is simple: the service joins the swarm on your behalf.
This shift results in a completely different transactional flow.
The Hand-off: You give a magnet link or torrent file to the debrid service. This is the last time you touch the P2P ecosystem. Your role as a peer is over before it begins.
The Ghost in the Machine: The service's high-bandwidth servers then join the swarm as a peer. They connect to other peers, download the pieces, and fulfill any seeding obligations. From the swarm's perspective, the debrid service is just another participant. Your IP address is nowhere to be found. It’s a clever piece of architectural sleight of hand—the swarm sees a participant, but it's a proxy.
The Emergent Cache: As the service fetches the complete file, it stores it in its own cache. This is where the magic happens. If another user ever requests that same torrent, the P2P step is skipped entirely. The service simply serves the file from its cache. What starts as a simple proxy service evolves, through user demand, into a massive, distributed file library. It’s a fascinating example of a system optimizing itself over time.
The Final Mile: The service then presents you with a simple, secure HTTPS link. You download the complete file directly from their servers. The chaos of the swarm is replaced by the clean, predictable nature of a direct download.
An Anatomy of the Advantages
This architectural shift isn't just a neat trick; it fundamentally solves the protocol's core trade-offs.
Decoupling Identity from Action: The most profound change is the abstraction of your identity. By delegating the P2P interaction to the service, your IP address is never exposed to the swarm. The debrid service acts as a buffer, ensuring the privacy of the end-user without the performance overhead or complexity of a VPN.
Escaping the Tyranny of the Swarm: Your download speed is no longer coupled to the health of the swarm. A torrent with only one slow seeder can be patiently downloaded by the debrid service's 24/7 servers and then delivered to you at maximum speed.
From Protocol Chaos to HTTPS Simplicity: The service handles all the complexities of the BitTorrent protocol. For the user, the interaction is simplified to a standard web download. This has the significant side effect of bypassing most ISP-level traffic shaping that specifically targets and throttles P2P connections, as an encrypted HTTPS transfer is typically treated as priority traffic.
